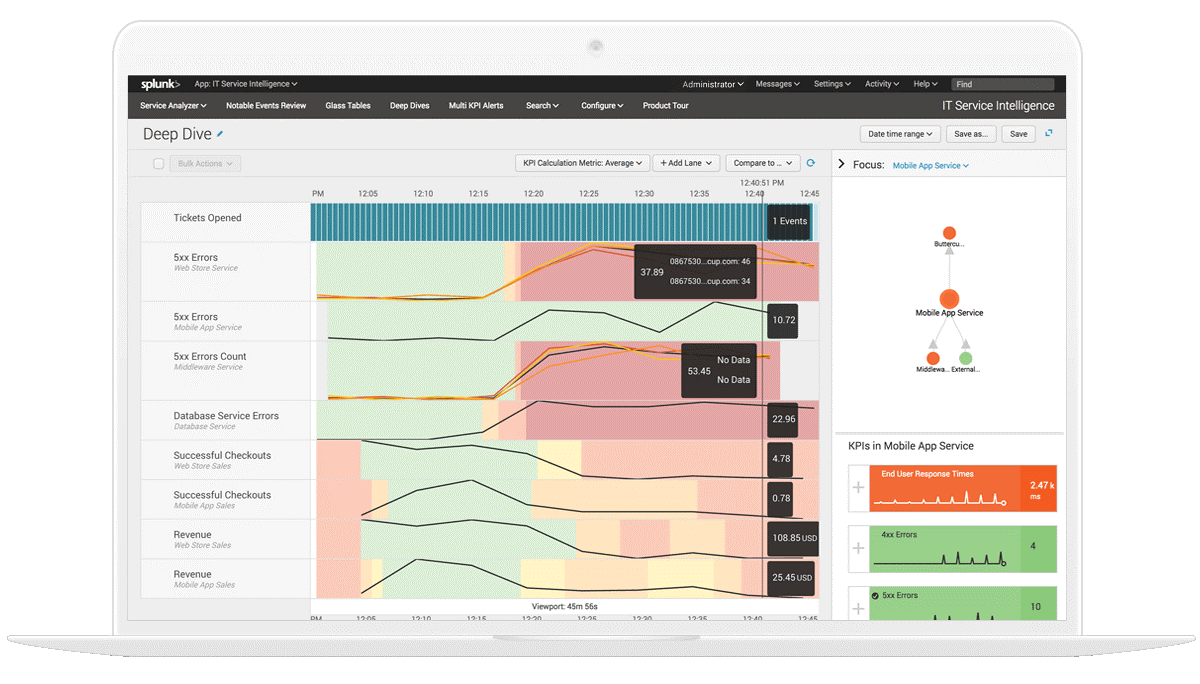
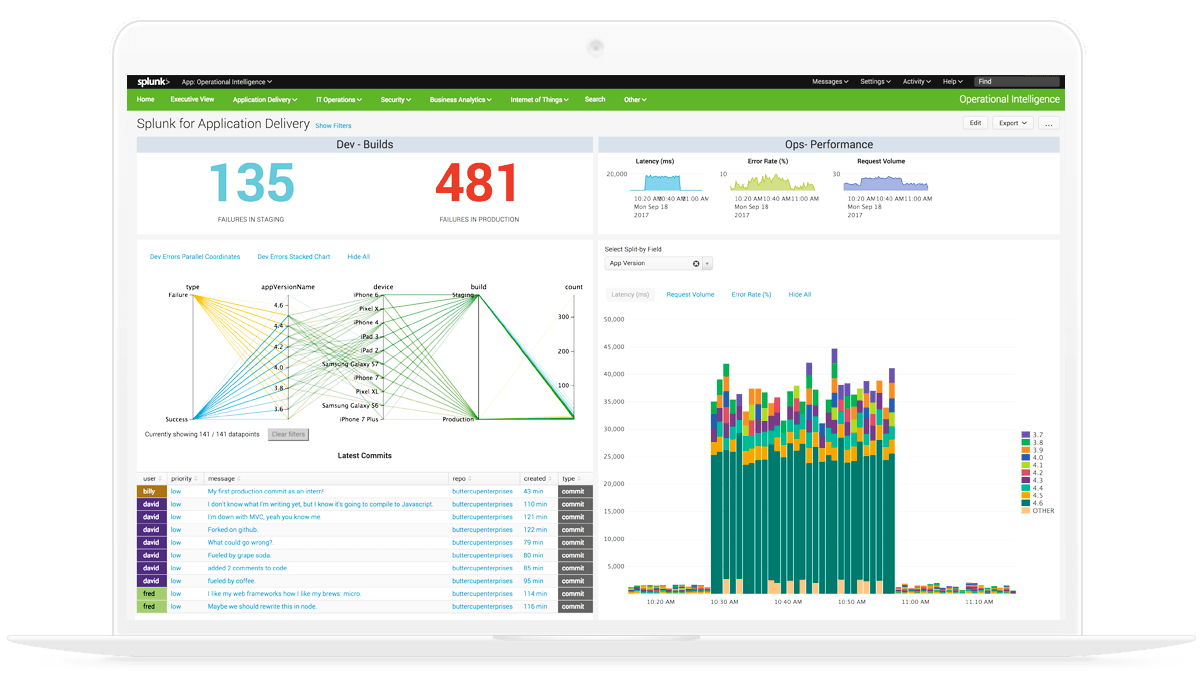
At A3Sec we are happy and we want to share with you the great news: we achieved the ISO 27001:2013 c...
Cybersecurity Blog
This is what we are passionate about and we want to
share it with you
I have implemented SIEM systems in the last 11 years of my life and always the challenges have been ...
At the end of 2009 I made the decision to stop being a provider and become a client. An opportunity ...
CISO Day 2019, the biggest event around the image of the CISO, will be held on June 12 at the Palaci...
Adoption of cloud solutions has advanced rapidly in the last two years as more organizations migrate...
"Power without control is useless" is the slogan of an old tire advertisement which emphasized the f...
How much importance do companies attach to cybersecurity? Although we are in an era where digital se...
Currently there are methodologies and best practices, such as SCRUM, DevOps, etc, for a fast softwar...
The concept of threat hunter is increasingly gaining strength within operational security teams. But...


.png)