Cyber telemetry engine and architecture of detection and response as a service
Specialised in the best management to reduce vulnerabilities in digital environments.
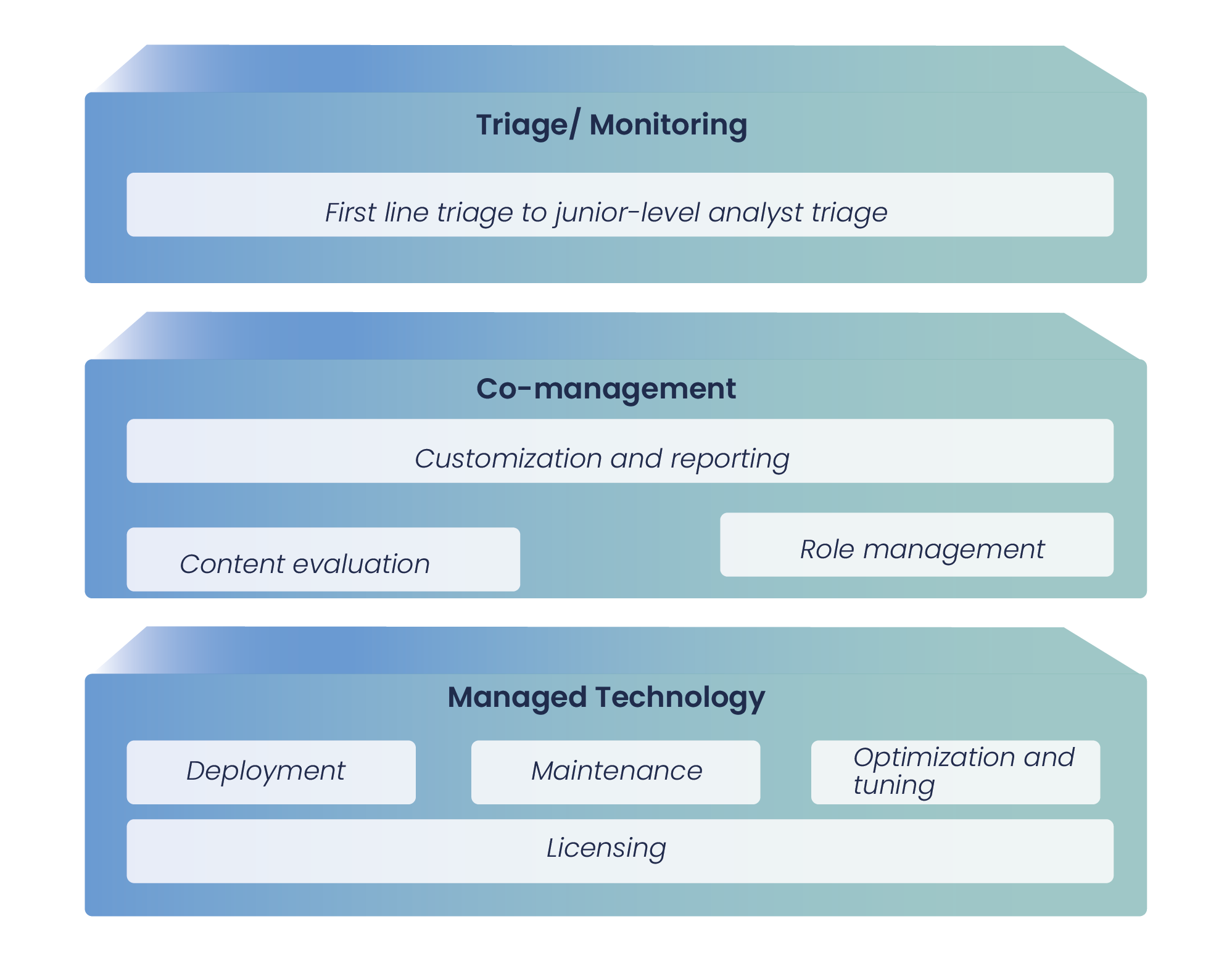
Description
Detection and response architecture services
The Cyber Telemetry Engine and Detection and Response Architecture is an advanced approach that combines real-time data collection, analysis and correlation with effective security incident response strategies. This system integrates telemetry technologies with detection and response tools to provide complete visibility of assets, activities and threats within an organisation.
Challenges
The accelerated evolution of cyber threats and the increased complexity of digital environments demand a constant updating of tools and approaches, generating constant challenges in the cybersecurity field.
Lack of comprehensive visibility
Many organisations do not have a complete view of their networks, endpoints, applications and cloud environments, making it difficult to identify threats and suspicious activity.
Data overload and alerts
Security teams face an overwhelming volume of data and alerts, many of which are false positives, making prioritisation of true threats a challenge.
Long detection and response time
Late threat detection or slow response allows attacks to spread, compromise critical systems and cause significant damage to the organisation.
Advanced threat identification
Sophisticated attacks, such as ransomware and APTs, employ evasive tactics to circumvent traditional security controls and operate undetected.
Lack of coordination between tools and equipment
Fragmented security solutions and isolated teams make effective incident coordination difficult.
Gaps in automatic remediation
Reliance on manual responses to incidents slows reaction and reduces efficiency, giving threats time to evolve and become more dangerous.
Difficulty adapting to evolving threats
Cyber threats are constantly changing, making static defences insufficient to ensure security.
Lack of comprehensive visibility
Many organisations do not have a complete view of their networks, endpoints, applications and cloud environments, making it difficult to identify threats and suspicious activity.
Data overload and alerts
Security teams face an overwhelming volume of data and alerts, many of which are false positives, making prioritisation of true threats a challenge.
Long detection and response time
Late threat detection or slow response allows attacks to spread, compromise critical systems and cause significant damage to the organisation.
Advanced threat identification
Sophisticated attacks, such as ransomware and APTs, employ evasive tactics to circumvent traditional security controls and operate undetected.
Lack of coordination between tools and equipment
Fragmented security solutions and isolated teams make effective incident coordination difficult.
Gaps in automatic remediation
Reliance on manual responses to incidents slows reaction and reduces efficiency, giving threats time to evolve and become more dangerous.
Difficulty adapting to evolving threats
Cyber threats are constantly changing, making static defences insufficient to ensure security.
Use cases
We provide comprehensive, real-time visibility of all assets and their exposure. We identify security breaches before they are exploited, using advanced tools to continuously map and monitor all assets, including unknown assets. Our dynamic inventory with up-to-date metadata enables effective risk assessment and prioritisation.
-
Case 1
Comprehensive visibility and real-time security
Solution
The telemetry engine collects real-time data from across the digital ecosystem, providing a unified view to map the attack surface and proactively detect security breaches.
Result
It provides a complete, real-time view of the entire digital environment, allowing vulnerabilities to be identified and mitigated before they become critical threats.
-
Case 2
Prioritisation of alerts
Solution
Using artificial intelligence, machine learning and pre-defined rules, our solution uses advanced analytics and correlation algorithms to filter out irrelevant data, reduce noise and prioritise critical alerts, improving threat detection and response.
Result
Prioritisation of alerts, enabling an agile and focused response to what is really important for the security of the organisation.
-
Case 3
Agile incident detection and response
Solution
It detects anomalies in real time and triggers automated responses, such as incident containment or isolation of compromised systems, reducing MTTD and MTTR.
Result
Minimize incident propagation and protect critical infrastructure. Streamline incident management, enabling rapid action that proactively isolates compromised systems and prevents attacks from spreading to other assets or areas of the network.
-
Case 4
Identifying advanced threats
Solution
Analyzes behavioral patterns and uses cyber intelligence to identify malicious activity even if it hasn’t been seen before. Detects threats based on techniques and tactics documented in frameworks such as MITRE ATT&CK.
Result
Detecting and neutralizing threats before they cause damage, gaining a deep understanding of attacker techniques and tactics to facilitate a precise and contextualized response, generating continuous protection that minimizes exposure time and reduces the potential impact of attacks.
-
Case 5
Efficient coordination between tools and equipment
Solution
Integrates multiple security tools into a centralized system, enabling fluid orchestration of detection and response. It also facilitates communication and collaboration between IT and security teams.
Result
It reduces duplication of efforts and enables better use of both technology and human talent. It also promotes informed and coordinated decision-making, strengthening the overall security posture.
-
Case 6
Safe and effective automatic remediation
Solution
Automate responses such as access revocation, vulnerability patching, and threat containment in real time, reducing reliance on human intervention and streamlining remediation.
Result
Reduces incident response time and the possibility of errors, ensuring consistent application of security measures.
-
Case 7
Adapting to evolving threats
Solution
Uses machine learning to continuously update detection models. Adapts to emerging threats through simulations, continuous penetration testing, and predictive analytics.
Result
It enables you to identify emerging threats with greater accuracy, reducing false positives and optimizing response. It strengthens security posture and minimizes operational burden through efficient automation.
Contact
Cybersecurity doesn't wait, and neither should you. At A3Sec, we're ready to help you turn your company into an antifragile one, strengthening every aspect of your cybersecurity model against current and future threats.
Our specialized squads are here to design a customized strategy that fits your unique needs.
Fill out our form and one of our agents will get back to you as soon as possible.



