Threat Intelligence
Specialized in the best management to reduce vulnerabilities in digital environments.
Description
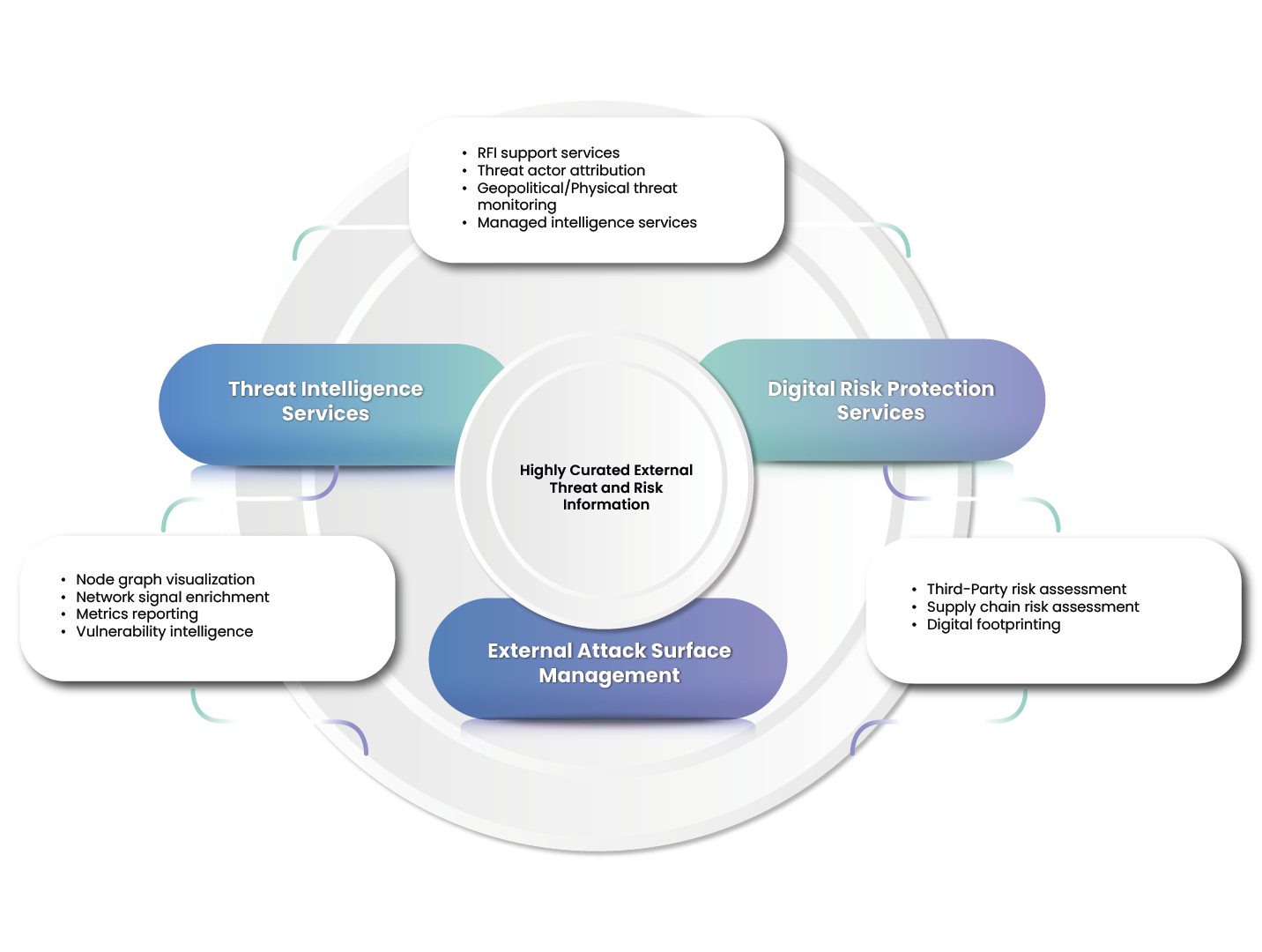
Threat Intelligence Services
Threat Intelligence Services is an advanced solution designed to collect, analyze, prioritize and provide actionable information on cyber threats. Its goal is to help organizations anticipate attacks, protect their most critical assets and make informed decisions to proactively mitigate risks.
The main aspects to take into account in threat modeling are the geopolitical context, the identification of the sector related to the target organization and a temporality added to the intelligence data that will be added to the prevention and detection capabilities.
Challenges
The accelerated evolution of cyber threats and the increased complexity of digital environments demand a constant updating of their tools and approaches, generating constant challenges in the field of cybersecurity.
Lack of visibility and strategic information on the threat landscape
Organizations often lack information about active or emerging threats targeting their sector, region, and/or infrastructure, making it difficult for leaders to make informed security decisions based on clear, actionable data.
Inefficient risk fragmentation and prioritization
The overload of alerts and indicators of compromise (IoCs) and the lack of integration between security tools and teams makes prioritization and coordinated response difficult.
Limited detection and late reaction to threats
Organizations often respond to threats after they have caused damage, rather than in advance of them. This scenario is further complicated by the detection of internal threats, such as malicious employees or negligence, which require specific intelligence for early identification.
Sophisticated and evasive threats
The tactics, techniques and procedures (TTPs) used by attackers are becoming more advanced, making them difficult to detect with traditional tools.
Expanding attack surface
Digital transformation and the rise of cloud assets, IoT devices and hybrid environments have significantly expanded the attack surface, making it more difficult to monitor and protect.
Lack of visibility and strategic information on the threat landscape
Organizations often lack information about active or emerging threats targeting their sector, region, and/or infrastructure, making it difficult for leaders to make informed security decisions based on clear, actionable data.
Inefficient risk fragmentation and prioritization
The overload of alerts and indicators of compromise (IoCs) and the lack of integration between security tools and teams makes prioritization and coordinated response difficult.
Limited detection and late reaction to threats
Organizations often respond to threats after they have caused damage, rather than in advance of them. This scenario is further complicated by the detection of internal threats, such as malicious employees or negligence, which require specific intelligence for early identification.
Sophisticated and evasive threats
The tactics, techniques and procedures (TTPs) used by attackers are becoming more advanced, making them difficult to detect with traditional tools.
Expanding attack surface
Digital transformation and the rise of cloud assets, IoT devices and hybrid environments have significantly expanded the attack surface, making it more difficult to monitor and protect.
Use cases
We provide real-time, end-to-end visibility of all assets and their exposure. We identify security gaps before they are exploited, using advanced tools to continuously map and monitor all assets, including unknown ones. Our dynamic inventory with up-to-date metadata enables effective risk assessment and prioritization.
-
Case 1
Advanced detection and analysis of TTPs
Solution
We use threat intelligence to identify indicators of compromise (IoC) associated with APT groups, such as malicious domains, IP addresses, malware signatures, and TTP techniques recognized in the MITRE ATT&CK matrix.
We map attacker tactics and techniques to the MITRE ATT&CK framework, making it easy to create targeted rules and alerts to strengthen the security of the corporate environment.Result
Early detection of long-term attacks and emerging attack techniques to enable security teams to act proactively before incidents materialize. -
Case 2
Correlation and prioritization of alerts
Solution
We integrate threat intelligence feeds into the SIEM to correlate alerts and provide context (for example, correlating suspicious activity alerts with known indicators of compromise or techniques).
Result
Reduction of false positives, focusing analysts' efforts on high-impact and high-probability threats.
-
Case 3
Vulnerability research and attack surface assessment
Solution
We use threat intelligence to identify and monitor new critical vulnerabilities, related exploits, and new attack vectors, including exposed assets, misconfigurations, or vulnerabilities in external infrastructure.
We analyze and block known exploits, allowing us to prioritize risk remediation and reduce the attack surface.
Result
Prioritizing patching to protect against targeted attacks and minimizing exposure by identifying and mitigating vulnerabilities before attackers discover them.
-
Case 4
Protection and monitoring of phishing, social engineering and dark web
Solution
We use threat intelligence to identify ongoing phishing campaigns and correlate them with current trends, integrating this information into email platforms and web services to block malicious sites. Additionally, we track mentions of the organization on dark web websites, including cybercriminal forums, stolen data marketplaces, and other underground communication channels.
Result
Protection against credential theft and attacks that exploit human trust.
Detecting data breaches and potential compromises at early stages, before they are actively used in attacks. -
Case 5
Monitoring vulnerabilities in the supply chain
Solution
We verify software and hardware vendors, as well as emerging vulnerabilities that could be exploited by malicious actors.
We integrate threat intelligence to assess the risks associated with third parties that have access to the organization's network.Result
Protection against compromises that exploit trust in third-party vendors.
-
Case 6
Proactive threat assessment and post-compromise analysis
Solution
We use threat intelligence to guide the proactive hunt for malicious actors within the organization's network by analyzing traffic patterns, logs, and anomalous behavior.
We investigate post-compromise techniques, such as lateral movement, privilege escalation, and data exfiltration, allowing forensic teams to identify the attacker's steps after an incident.Result
Detection of threats that are difficult to identify with automated solutions, based on manual analysis and context provided by threat intelligence. Improves incident response capabilities by enabling a deeper understanding of the attack and its consequences. -
Case 7
Threat intelligence reports and third-party alerts
Solution
We integrate threat intelligence capabilities into the incident response (IR) workflow. This can include automating the identification of actors, tactics, and techniques used, accelerating incident containment and remediation.
Result
Acceleration of response and reduction in downtime and incident impact.
Contact
Cybersecurity doesn't wait, and neither should you. At A3Sec, we're ready to help you turn your company into an antifragile one, strengthening every aspect of your cybersecurity model against current and future threats.
Our specialized squads are here to design a customized strategy that fits your unique needs.
Fill out our form and one of our agents will get back to you as soon as possible.


