Management of theExposure and Attack Surface
Specialised in the best management to reduce vulnerabilities in digital environments.
Description
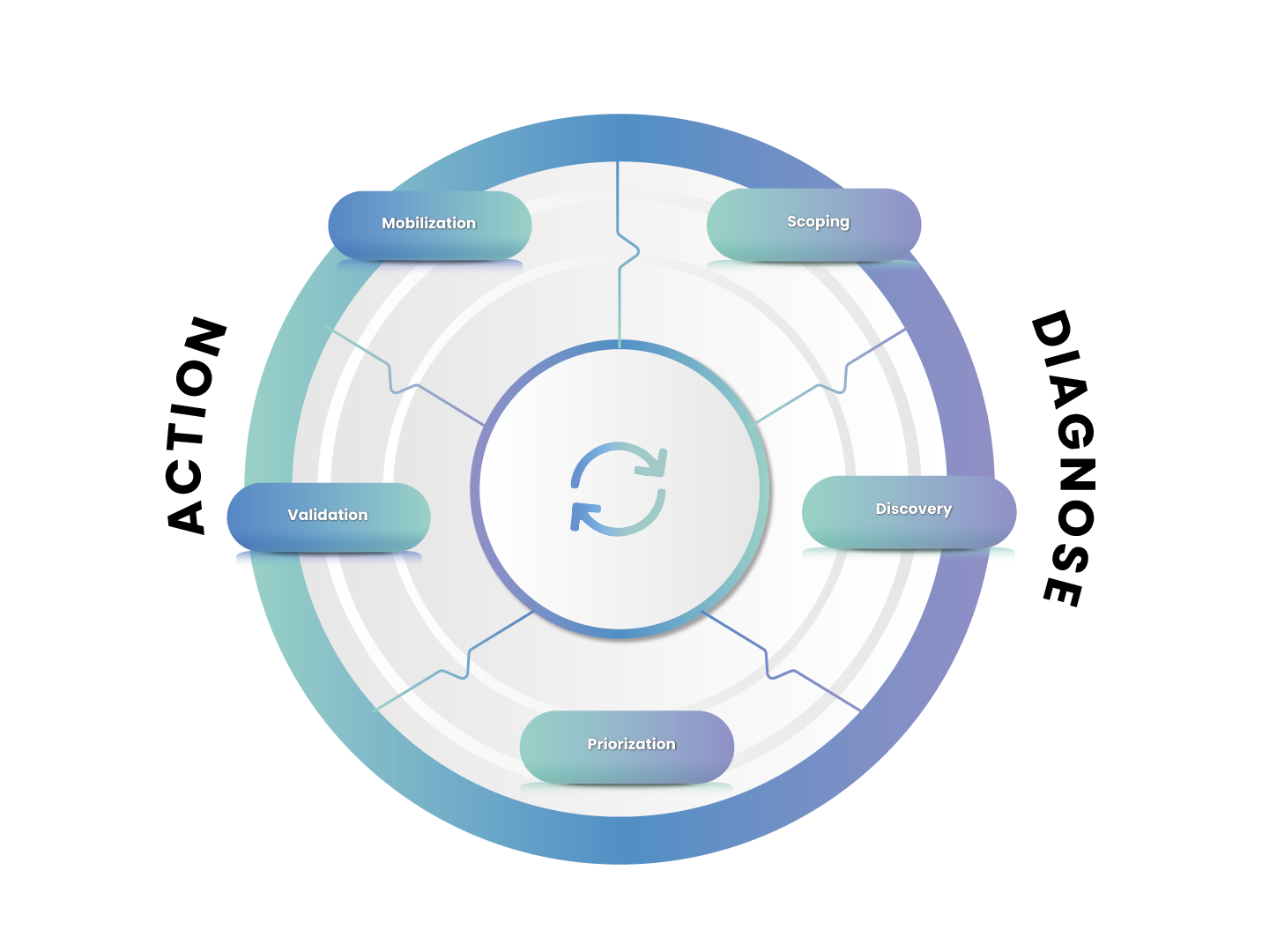
Continuous ThreatExposure Management (CTEM)
CTEM is an innovative and dynamic strategy for the proactive management of cyber security threats in an organisation. Through a structured and continuous approach, it efficiently identifies, prioritises, validates and mitigates risks, ensuring comprehensive protection against evolving threats.
This service combines advanced vulnerability assessment technologies, threat intelligence and simulations of real attacks to provide a clear and prioritised view of the most critical risks. By implementing CTEM, companies can strengthen their cyber security, minimise security breaches and protect their most valuable assets from cyber-attacks.
Challenges
The accelerated evolution of cyber threats and the increased complexity of digital environments demand a constant updating of tools and approaches, generating constant challenges in the field of cyber security.
Expanding attack surface and exposure to threats
Digitalisation and the rise of the cloud and IoT expand the attack surface, making it harder to see and increasing the exposure of assets to cyber threats.
Inefficient prioritisation and validation of vulnerabilities
With thousands of vulnerabilities identified on a regular basis, organisations face difficulties in deciding which ones to address first, especially if they lack effective processes to validate whether they can be exploited in a real environment.
Difficulties in the ongoing management of risks and hazards
Traditional risk management models are often static and rely on ad hoc rather than continuous approaches, which makes them insufficient to address dynamic threats and limits the ability of organisations to adapt to a changing landscape.
Inefficient communication and long remediation time
Security teams often face difficulties in communicating risks and coordinating remediation actions, causing vulnerabilities to remain unresolved for long periods.
Inability to adapt to emerging threats
Organisations need to adapt to a constantly evolving threat landscape.
Regulatory compliance and reporting
Complying with cybersecurity regulations and demonstrating adequate risk management can be a challenge.
Expanding attack surface and exposure to threats
Digitalisation and the rise of the cloud and IoT expand the attack surface, making it harder to see and increasing the exposure of assets to cyber threats.
Inefficient prioritisation and validation of vulnerabilities
With thousands of vulnerabilities identified on a regular basis, organisations face difficulties in deciding which ones to address first, especially if they lack effective processes to validate whether they can be exploited in a real environment.
Difficulties in the ongoing management of risks and hazards
Traditional risk management models are often static and rely on ad hoc rather than continuous approaches, which makes them insufficient to address dynamic threats and limits the ability of organisations to adapt to a changing landscape.
Inefficient communication and long remediation time
Security teams often face difficulties in communicating risks and coordinating remediation actions, causing vulnerabilities to remain unresolved for long periods.
Inability to adapt to emerging threats
Organisations need to adapt to a constantly evolving threat landscape.
Regulatory compliance and reporting
Complying with cybersecurity regulations and demonstrating adequate risk management can be a challenge.
Use Cases
We provide comprehensive, real-time visibility of all assets and their exposure. We identify security breaches before they are exploited, using advanced tools to continuously map and monitor all assets, including unknown assets. Our dynamic inventory with up-to-date metadata enables effective risk assessment and prioritisation.
-
Case 1
Comprehensive visibility and proactive asset management
Solution
We provide a comprehensive, real-time view of all assets and their level of exposure.
We identify gaps in infrastructure and applications before they are exploited.
We use advanced discovery tools to continuously map and monitor all assets, including unknown assets.
We integrate a dynamic inventory with up-to-date metadata to effectively assess and prioritise risks. -
Case 2
Efficient vulnerability management
Solution
We implement automated attack solutions and manual Red Teaming exercises to confirm threat exploitability.
We provide detailed analysis of the potential impact and responsiveness of the security team.
We prioritise vulnerabilities based on context, potential impact and likelihood of exploitation.
We facilitate an approach based not only on risk, but also on intelligence and business, to optimise available resources. -
Case 3
Dynamic and adaptive risk and threat management
Solution
We implement continuous, adaptive risk management.
We constantly monitor the threat environment to adjust defences in real time.
We offer a continuous service that ensures constant threat assessment and scope adaptation according to evolving risks.
We design a progressive maturity plan to integrate security as an iterative and scalable process. -
Case 4
Optimisation of communication flows and remediation
Solution
We improve remediation workflows through automation and prioritisation.
We significantly reduce risk exposure time.
We establish clear communication flows and defined processes to prioritise and manage threats.
We facilitate team mobilisation through assignment of responsibilities, clear timelines and tracking tools. -
Case 5
Anticipating and adapting to emerging threats
Solution
We use cyber intelligence to identify emerging threats and proactively adjust strategies.
We enable simulations and predictive analytics to anticipate new risks. -
Case 6
Regulatory compliance
Solution
We generate automated and detailed reports that meet regulatory standards.
We help organisations demonstrate their preparedness and commitment to cyber security.
Resources





Contact
Cybersecurity doesn't wait, and neither should you. At A3Sec, we're ready to help you make your business anti-fragile, strengthening every aspect of your cyber security model against current and future threats.
Our specialised squads are here to design a customised strategy that fits your unique needs.
Fill out our form and one of our agents will contact you as soon as possible.
