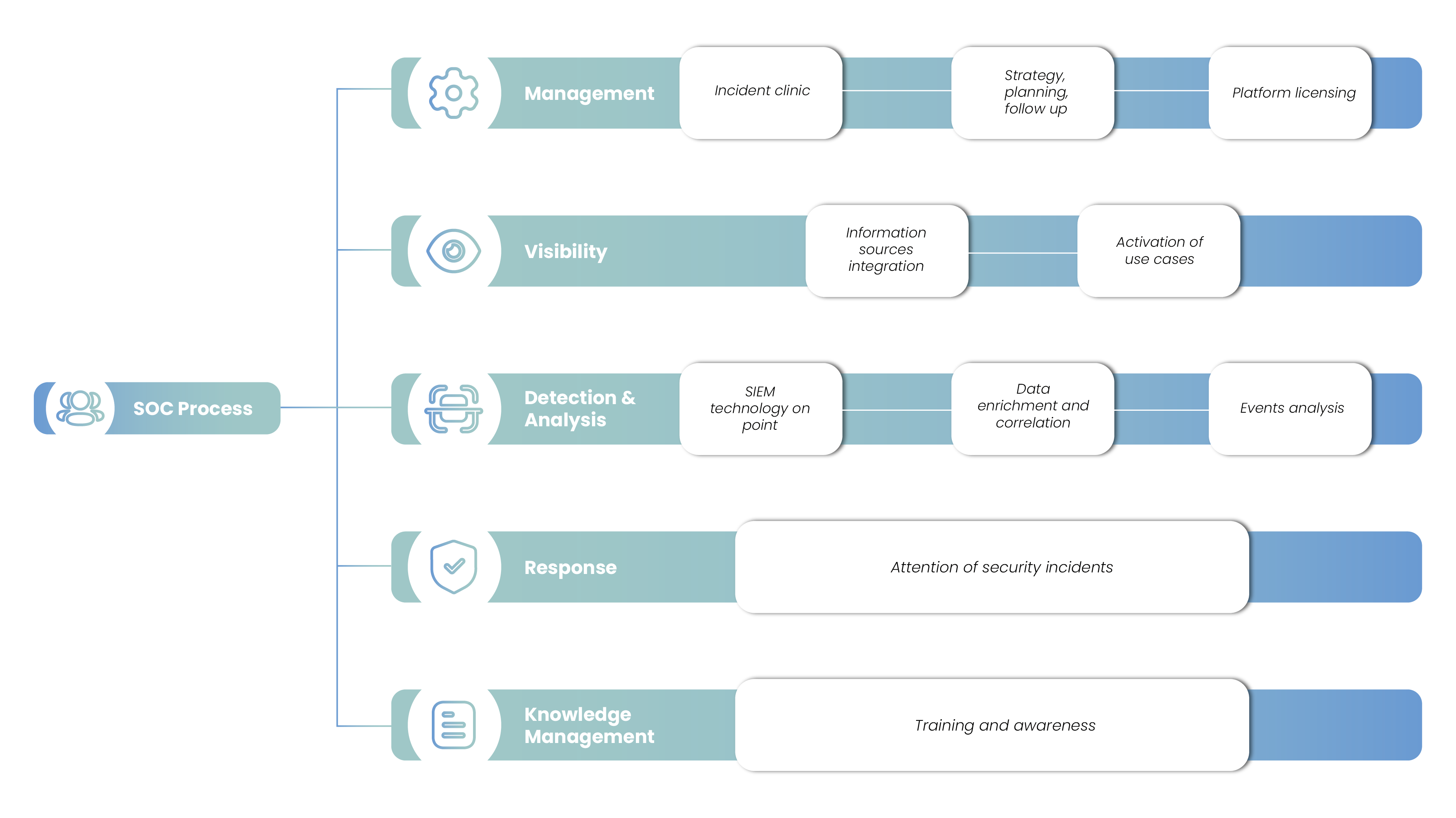
Incident detection and containment
Specialized in the best management to reduce vulnerabilities in digital environments.
Description
Incident detection and containment services
Our Incident Detection and Containment Services combine advanced technology, structured processes and specialized teams to identify and contain cyberattacks before they significantly impact organizations’ operations. Their effectiveness is reflected in key indicators such as Mean Time to Detection (MTTD) and Mean Time to Response (MTTR), which demonstrate the speed in detecting and resolving incidents, ensuring greater availability and security.
Challenges
The accelerated evolution of cyber threats and the increased complexity of digital environments demand a constant updating of their tools and approaches, generating constant challenges in the field of cybersecurity.
Security alert overload
Security tools generate large volumes of alerts, many of which are false positives, making it difficult to identify real threats that have already materialized.
Long threat detection time
Threats can remain undetected for weeks or months, increasing their potential impact.
Rapid spread of attacks
Threats such as ransomware or lateral attacks spread rapidly across the network if not contained in time.
Sophisticated and evasive threats
Attackers use advanced tactics, such as ransomware and fileless attacks, that evade traditional security controls.
Disorganized management of security events and incidents
Cyberattacks can disrupt critical operations, causing financial and reputational losses. Additionally, many organizations lack structured processes for escalating and reacting to incidents, leading to delays in containment.
Lack of specialized resources
Many organizations do not have enough or trained cybersecurity personnel to handle complex incidents.
Security alert overload
Security tools generate large volumes of alerts, many of which are false positives, making it difficult to identify real threats that have already materialized.
Long threat detection time
Threats can remain undetected for weeks or months, increasing their potential impact.
Rapid spread of attacks
Threats such as ransomware or lateral attacks spread rapidly across the network if not contained in time.
Sophisticated and evasive threats
Attackers use advanced tactics, such as ransomware and fileless attacks, that evade traditional security controls.
Disorganized management of security events and incidents
Cyberattacks can disrupt critical operations, causing financial and reputational losses. Additionally, many organizations lack structured processes for escalating and reacting to incidents, leading to delays in containment.
Lack of specialized resources
Many organizations do not have enough or trained cybersecurity personnel to handle complex incidents.
Use cases
We provide real-time, end-to-end visibility of all assets and their exposure. We identify security gaps before they are exploited, using advanced tools to continuously map and monitor all assets, including unknown ones. Our dynamic inventory with up-to-date metadata enables effective risk assessment and prioritization.
-
Case 1
Optimizing and prioritizing security alerts
Solution
We develop use cases oriented to TTPs according to the context of the clients, providing testing and quality processes at the time of deploying them to production, thus guaranteeing the reduction of false positives from the beginning.
The Incident Clinic strategy addresses the problem of alert fatigue from the strategic and operational fronts, allowing to adequately reduce the risks associated with this situation.Result
Alert filtering and prioritization using advanced correlation algorithms and contextual intelligence.
Operational noise is reduced so teams can focus on the most critical threats. -
Case 2
Proactive monitoring and rapid threat containment
Solution
We provide continuous, real-time monitoring, using artificial intelligence and advanced tools to quickly identify anomalous activities.
We implement immediate containment measures, such as isolating network segments or shutting down malicious processes.Result
Reduces mean time to detection (MTTD), minimizing risk exposure.
Limits the scope of the attack before it compromises more systems. -
Case 3
Advanced detection with intelligence and automation
Solution
We work to achieve the maturity of detection processes, in order to evaluate the capacity of security operations to identify anomalies. To do this, we take into account the quality and volume of the data collected, and the interpretation and analysis capabilities of different types of data.
We implement detection strategies that address fronts such as the collection, analysis, prioritization and contextualization of threats that may impact an organization. Later, by applying methodologies such as MaGma, we manage and administer the implementation of new use cases, associating TTPs, expanding visibility and coverage in detection processes.
We apply hyper-automation to achieve automated mapping of security operations, zero-day threat coverage and threat modeling, reducing the MTTD of security operations.Result
Detection of sophisticated threats through analysis of anomalous behavior and patterns.
Application of frameworks such as MITRE ATT&CK to identify tactics and techniques used by attackers. -
Case 4
Orchestration and agile response to security incidents
Solution
We act efficiently with specialized personnel, providing recommendations to contain and mitigate activities that may be precursors to a security incident, ensuring that critical systems are operational again as soon as possible.
Result
Development and implementation of automatic and manual actions (playbooks) to contain threats, such as isolating compromised devices or blocking malicious users. -
Caso 6
Specialized and continuous support in cybersecurity
Solution
They provide access to cybersecurity experts 24/7 to manage critical incidents.
Result
Complements organizations' internal teams with specialized services, such as advanced investigation and containment.
Resources











Contact
Cybersecurity doesn't wait, and neither should you. At A3Sec, we're ready to help you turn your company into an antifragile one, strengthening every aspect of your cybersecurity model against current and future threats.
Our specialized squads are here to design a customized strategy that fits your unique needs.
Fill out our form and one of our agents will get back to you as soon as possible.
