Crisis Management andIncident Response
Specialised in the best management to reduce vulnerabilities in digital environments.
Description
Crisis management and incident responseservices
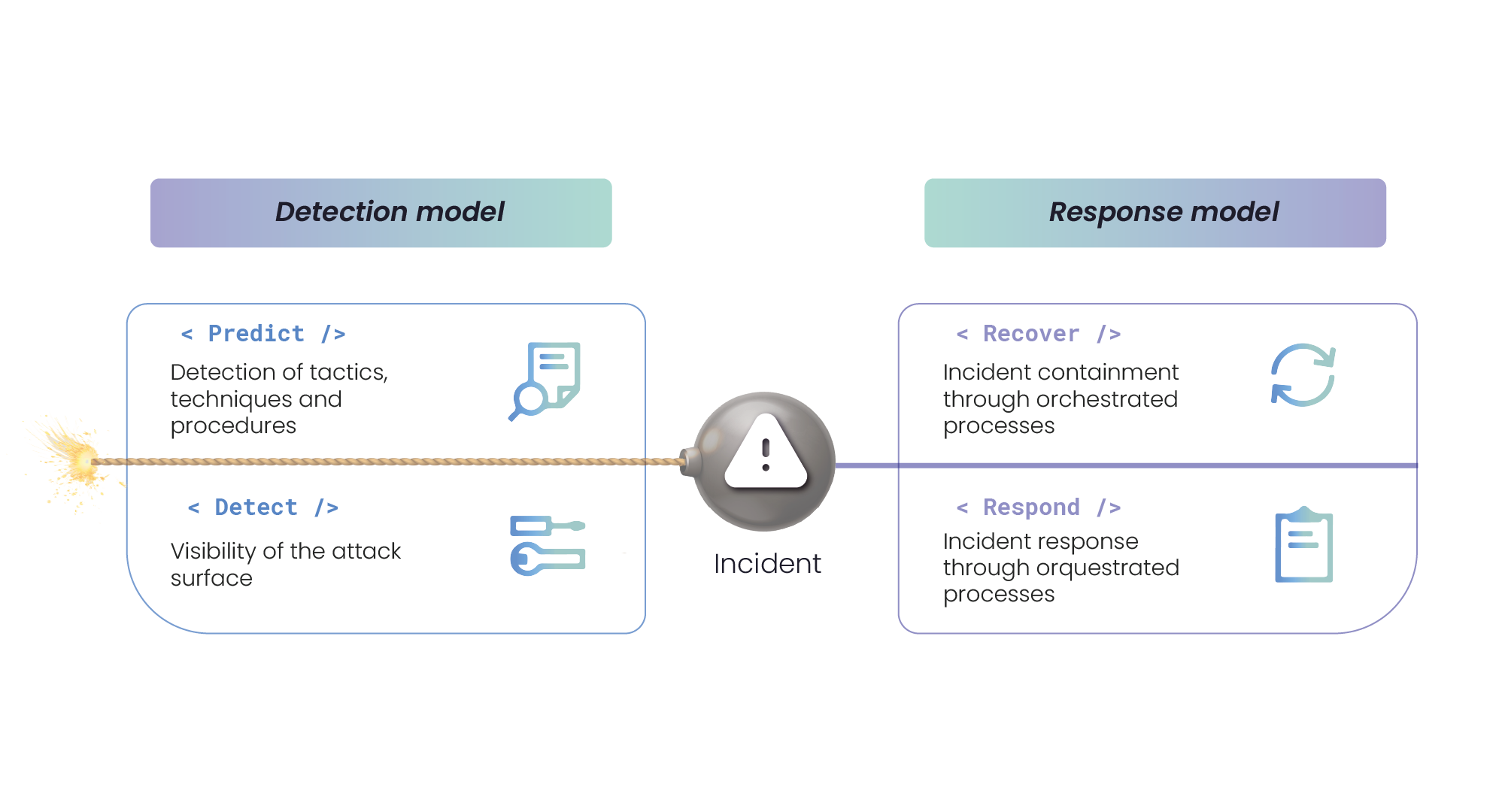
Crisis Management and Incident Response Services provide a comprehensive solution to prepare for, manage and respond to cyber security incidents, minimising the potential impact on the organisation and ensuring business continuity. The services include the planning and execution of specific actions to identify, contain, eradicate and recover from incidents. This is achieved through the use of threat intelligence, structured response processes and highly qualified personnel.
Challenges
The accelerated evolution of cyber threats and the increased complexity of digital environments demand a constant updating of tools and approaches, generating constant challenges in the cybersecurity field.
Outdated plans and procedures
Shortage of continuity tests with realistic approaches
Lack of early detection
Limited visibility in systems
Shortage of trained personnel
Continuous evolution of threats
Challenges in collaborating with CSPs
Outdated plans and procedures
Shortage of continuity tests with realistic approaches
Lack of early detection
Limited visibility in systems
Shortage of trained personnel
Continuous evolution of threats
Challenges in collaborating with CSPs
Use Cases
We provide comprehensive, real-time visibility of all assets and their exposure. We identify security breaches before they are exploited, using advanced tools to continuously map and monitor all assets, including unknown assets. Our dynamic inventory with up-to-date metadata enables effective risk assessment and prioritisation.
-
Case 1
Assessment and development of incident response plan.
Solution
Highly qualified personnel evaluate the construction and testing of the cybersecurity incident response plans defined by the organisation, as well as the technical plans for the mitigation of different threats.
Result
Defines structured procedures to identify, isolate and mitigate the incident quickly, minimising damage.
Implement crisis management plans that include defined roles and responsibilities, clear lines of communication and decision protocols (playbooks).
Conduct detailed simulation and post-mortem exercises to identify areas for improvement and update response policies. -
Case 2
Root cause identification and analysis
Solution
We collect and analyse digital artefacts to identify potential vulnerabilities, attacker TTPs (Tactics, Techniques and Procedures) and flaws in existing controls that were exploited by attackers causing an impact on the company's services.
Prioritisation tools are used based on the impact of the incident, the criticality of the affected systems and the available response capabilities.Result
High-level technical reports are produced describing the events generated by the attackers on the affected systems.
Generates improvement plans for prevention and timely response to future incidents.
Accompaniment until closure and implementation of lessons learned. -
Case 3
Preparation and training of the team
Solution
We develop table top/cyber simulation exercises, and cyber crisis training spaces to prepare technical and non-technical staff for cyber security incident response, management and recovery.
The focus of each of the simulations and workshops can vary according to the organisation's goals and target audience.Result
It provides technical skills so that technology teams can be up to date in detecting and containing threats to the company's cyberspace.
Capacita al personal técnico y no técnico con el objetivo de preparar a los diferentes equipos a la hora de atender un incidente.
Resources











Contact
Cybersecurity doesn't wait, and neither should you. At A3Sec, we're ready to help you make your business anti-fragile, strengthening every aspect of your cyber security model against current and future threats.
Our specialised squads are here to design a customised strategy that fits your unique needs.
Fill out our form and one of our agents will contact you as soon as possible.
